Key Rotation Settings
Detailed breakdown of the settings and functionalities available for this feature:
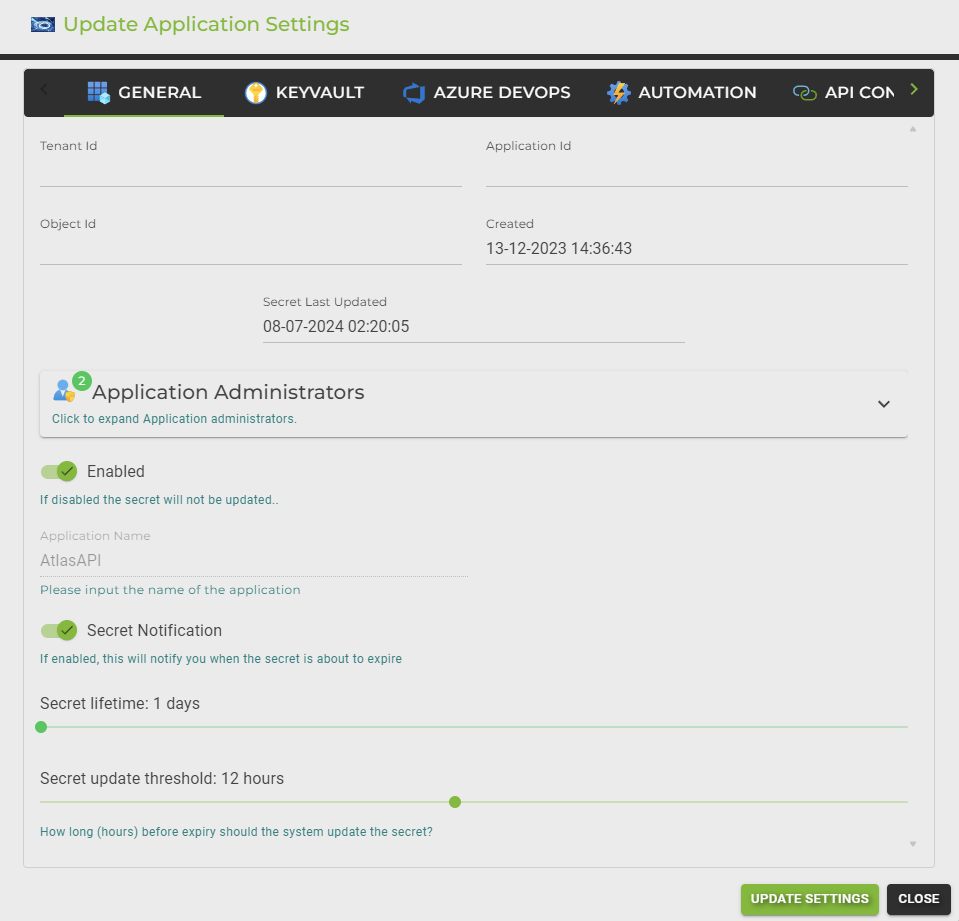
Tenant Id:
The unique identifier for your Azure tenant. This ensures that the secret rotation is performed within the correct tenant context.
Application Id:
This is the identifier of the application registration (service principal) whose secret will be rotated. It ensures that the correct application is targeted for secret updates.
Object Id:
The unique identifier of the service principal object. This is used to manage permissions and access controls within Azure.
Created:
The date and time when the service principal was created. This information can be useful for auditing and compliance purposes.
Secret Last Updated:
Indicates the last time the secret was updated. This helps track the rotation frequency and ensures that the secret is being updated as expected.
Application Administrators:
By default, the administrators will become owners of the app registrations. They will see the app registration here in AZExecute and can manage it accordingly. This section allows you to expand and view the list of administrators.
Enabled:
This toggle enables or disables the secret rotation for the selected application. If disabled, the secret will not be updated, which can be useful for maintenance or troubleshooting.
Application Name:
The name of the application registration. This helps identify the application within the AZExecute interface.
Secret Notification:
This option, when enabled, will notify you when the secret is about to expire. This provides an additional layer of security by ensuring that you are aware of upcoming secret expirations.
Secret Lifetime:
Defines the lifespan of the secret in days. This setting allows you to control how frequently the secret should be rotated to maintain security.
Secret Update Threshold:
Specifies the number of hours before the secret’s expiration when the system should update the secret. This ensures that the secret is always valid and avoids service interruptions.
Key Vault Integration
This section outlines the procedure to configure Key Vault integration for securely handling and updating service principal secrets via AZExecute. This feature simplifies secret management, ensuring that credentials are automatically updated and securely stored within your specified Azure Key Vault.
Selecting a Key Vault:
Enable Key Vault Integration: Toggle the "Key Vault Integration" switch to enable this feature. This activates the interface for Key Vault configuration within AZExecute.
Choose a Key Vault: From the "Key Vault" dropdown, select the desired Key Vault where you want the service principal secrets to be stored. The dropdown list is populated with Key Vaults you have access to within your Azure subscription. This ensures that the secret rotation targets the correct vault.
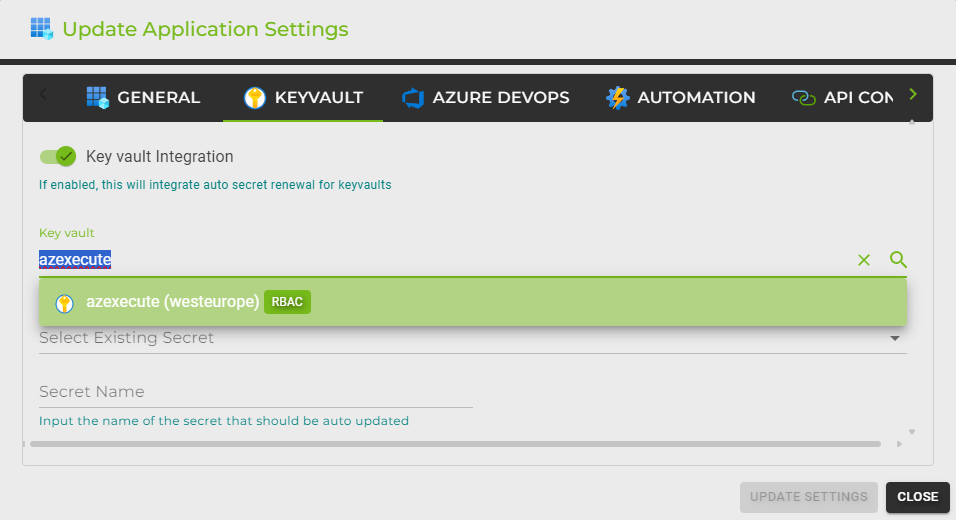
Configuring the Secret: Select Existing Secret or Create New:
Select Existing Secret: If the secret you intend to use already exists, you can select it from the dropdown menu labeled "Select Existing Secret." This is useful for integrating with existing configurations without creating additional secrets.
Create New Secret: If a new secret is required, type the name of the new secret in the "Secret Name" input field. This name will be used to create a new secret in the chosen Key Vault, where the updated service principal secret will be stored after each rotation.
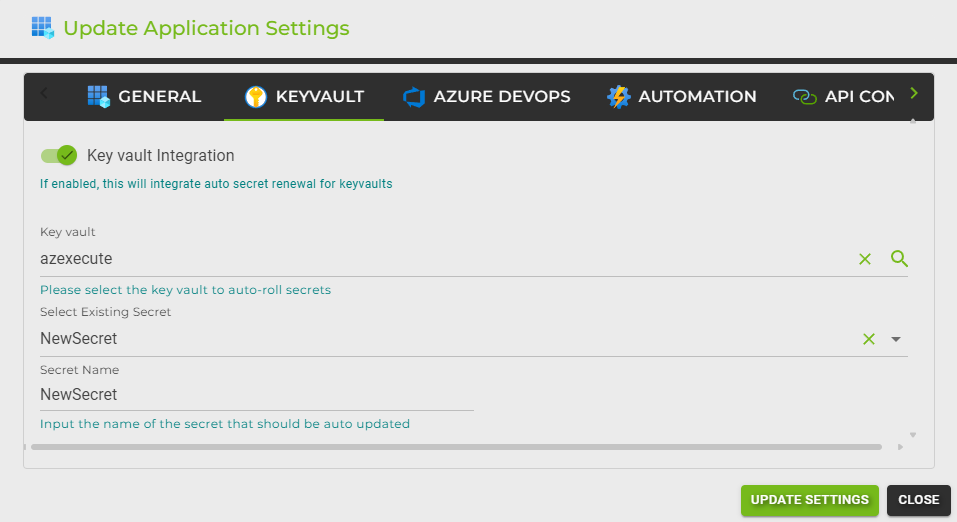
Automatic Updates: Once integrated, AZExecute will handle the rotation of the service principal's secret and ensure the new secret value is updated within the designated Key Vault automatically. This occurs according to the rotation policy defined in the "Secret Lifetime" and "Secret Update Threshold" settings.
Security Compliance: Integrating Key Vault ensures that all secret values are managed according to Azure's security standards, providing audit trails and access controls that are not possible if secrets are managed manually or stored in less secure locations.
Best Practices:
Regular Monitoring: Regularly monitor the integration to verify that secrets are rotated and updated as expected. Utilize Azure monitoring tools to get alerts on key vault operations.
Access Controls: Restrict access to the Key Vault strictly to entities that require it, minimizing the risk of unauthorized access.
Azure DevOps Integration
If OIDC connections are not feasible for your setup, this feature can automatically update Azure DevOps Service Connections with the new secret, maintaining continuous integration and delivery pipelines without disruption.
Requirements: Before you can enable this integration, ensure you are a member of the "Project/Endpoint Administrators" group in Azure DevOps. This permission is necessary to manage service connections and their credentials.
This feature requires that the user, has sufficient privileges to configure service connections within the selected Azure DevOps organization and project.
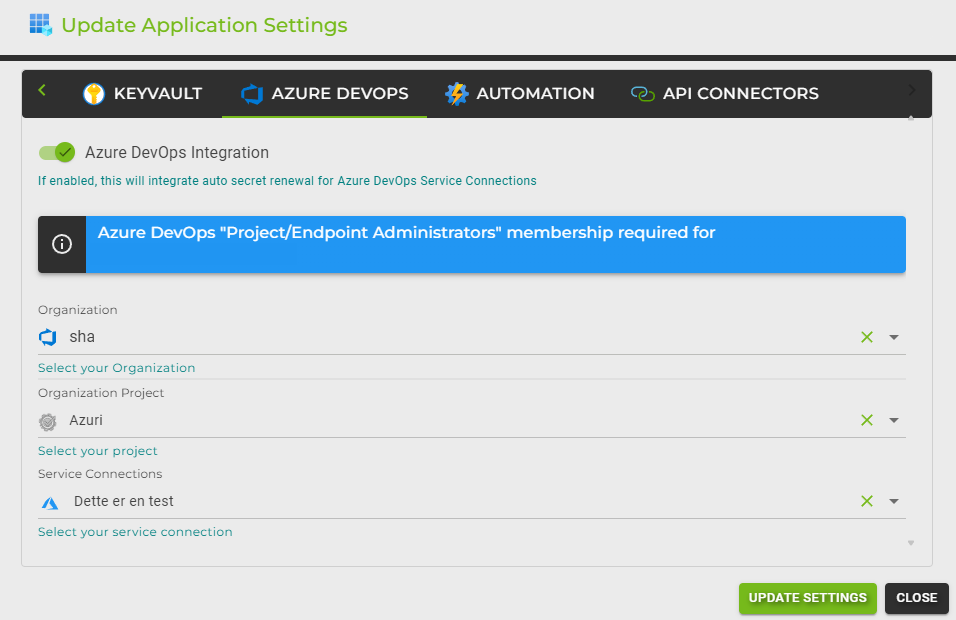
Configuration Steps:
Select Organization: From the "Organization" dropdown, select the Azure DevOps organization where the service connections are managed.
Select Project: Choose the Azure DevOps project that contains the service connections you wish to update automatically.
Select Service Connection: Pick the specific service connection for which the secrets should be auto-renewed. This selection ensures that the right connection is targeted for updates.
Once all settings are correctly configured, enable the integration to start automatic secret renewal. This process helps maintain your Azure DevOps service connections with up-to-date credentials, minimizing disruption and maintaining high security standards.
Automation Account Integration
Upon secret rotation, the system can automatically trigger an Azure Automation Runbook. This feature can pass the new secret to the runbook, enabling tasks such as updating service principals on on-premise systems via hybrid workers.
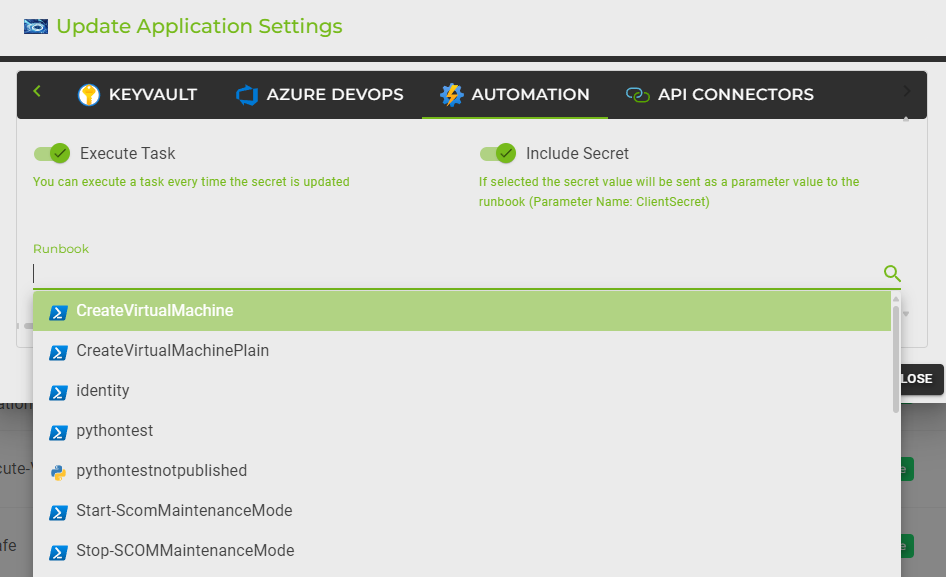
Include Secret:
If this option is selected, the secret value will be sent as a parameter value to the runbook. The parameter name used for this purpose is ClientSecret. This ensures that the runbook has access to the most recent secret when it runs.
Runbook:
Here, you can specify the runbook to be executed. You can select from a list of available runbooks. The runbooks listed may include various scripts and processes such as creating virtual machines, managing identities, and other custom automation tasks.
To select a runbook:
Click on the runbook input field to display a list of available runbooks.
Scroll through the list or use the search functionality to find the desired runbook.
Select the runbook from the dropdown list. The selected runbook will be executed each time the secret is updated.
Runbook Parameters:
When you select a runbook, you may see an information message indicating whether the runbook has a parameter named "ClientSecret". If the parameter does not exist, the secret will still be sent to the runbook but may not be utilized by it.
Runbook Start RunOn:
This setting allows you to choose where the runbook will execute. By default, it runs on Azure, but you can also select a hybrid worker if you have on-premise tasks that need to be executed.
To select a hybrid worker:
Click on the "Select a hybridworker" dropdown.
Choose the appropriate hybrid worker from the list to execute the runbook on-premise.
Additional Runbook Parameters:
If your runbook requires additional parameters, you can provide these in the input fields available. This allows you to pass custom values to the runbook at execution time.
Logic Apps API Connectors Update
This capability allows automatic updating of API connectors within Azure Logic Apps. It supports connectors for various services like storage accounts and key vaults, ensuring they always use the latest secrets for secure access.
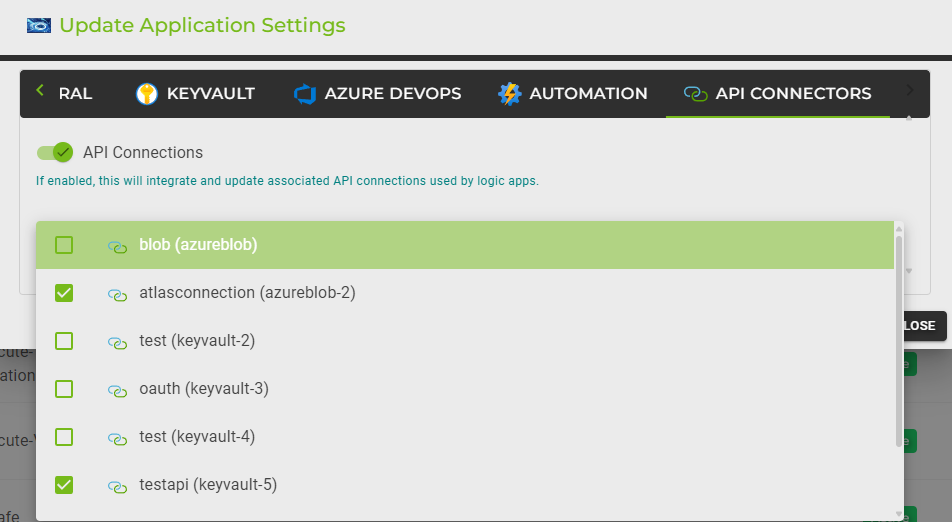
API Connections:
This feature enables the integration and updating of associated API connections used by Logic Apps. If enabled, AZExecute will automatically update the API connections with the new secret values, ensuring continuous and secure connections.
Select API Connections:
You can select the API connections that should be updated. These connections use service principals where the client ID and secret are provided. By enabling this feature, AZExecute can automatically rotate the secrets for these connections.
To select API connections:
Click on the API connections input field to display a list of available connections.
Scroll through the list to find the desired connections.
Select the connections by checking the boxes next to the connection names. Multiple connections can be selected if needed.
Connection Types:
The API connections can be for various services such as Azure Blob Storage, Key Vault, and others. Each connection type may have specific requirements for the client ID and secret.
If you encounter any issues or need further assistance, please contact us at
info@azexecute.com. Our support team is here to help you.
